A Strategic SWOT-Based Data Encryption Market Analysis
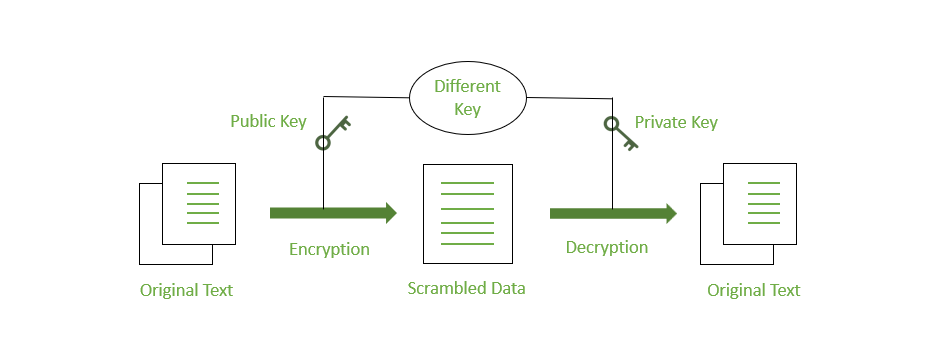
A comprehensive and strategic Data Encryption Market Analysis, when viewed through a SWOT (Strengths, Weaknesses, Opportunities, Threats) framework, provides a clear and balanced picture of the industry's dynamics. The market's most significant and undeniable strength is its status as a foundational and indispensable cybersecurity control. In the modern era of pervasive digital threats, encryption is no longer considered an optional extra but a mandatory requirement for any organization serious about protecting its data. This essential nature ensures a stable and consistently growing demand. Another core strength is encryption's direct and critical role in helping organizations meet stringent regulatory compliance obligations. With laws like GDPR and HIPAA imposing heavy penalties for data breaches, the investment in encryption becomes a clear-cut business decision driven by risk mitigation and legal necessity, rather than just technical preference. Furthermore, the mathematical robustness and public vetting of standardized algorithms like AES provide a high degree of reliability and engender trust among users, solidifying encryption's position as a dependable and effective security measure against a wide range of threats.
Despite its critical importance, the data encryption market is not without its inherent weaknesses. The primary challenge has always been the complexity of implementation and, more specifically, the daunting task of cryptographic key management. The security of an entire system rests on the protection of its keys; if a key is lost, the data it protects is irrecoverably lost, and if a key is stolen, the encryption is rendered useless. This operational complexity can be a significant barrier to adoption, particularly for small and medium-sized enterprises (SMEs) that lack dedicated cybersecurity expertise. Another significant weakness is the performance overhead associated with the encryption and decryption processes. These cryptographic operations consume CPU cycles and can introduce latency, which may negatively impact the performance of high-throughput applications, real-time systems, or large-scale databases. This trade-off between security and performance often requires careful architectural planning and can sometimes lead organizations to forgo encryption in performance-critical scenarios, creating potential security gaps and difficult risk acceptance decisions.
Looking forward, the market is brimming with substantial opportunities for growth and innovation. The continued exponential growth of data generated by cloud computing, mobile devices, and the Internet of Things (IoT) creates a constantly expanding addressable market for encryption solutions. A major opportunity lies in the delivery of simplified, cloud-native "Encryption-as-a-Service" and "Key-Management-as-a-Service" (KMaaS) offerings. These models abstract away the underlying complexity, allowing businesses to consume enterprise-grade encryption and key management as a simple utility, dramatically lowering the barrier to entry. The most significant long-term opportunity, however, is the development and commercialization of Post-Quantum Cryptography (PQC). As the theoretical threat of quantum computers becomes a practical reality, the entire world will need to migrate to new, quantum-resistant algorithms. This massive, mandatory technological refresh represents a multi-billion-dollar opportunity for vendors who can develop and lead the market with proven PQC solutions and the crypto-agility platforms needed to manage this complex, once-in-a-generation transition.
Conversely, the industry faces several potent threats that could undermine its foundations. The most profound and widely discussed threat is the future advent of fault-tolerant quantum computers. These powerful machines are predicted to be capable of breaking many of the asymmetric encryption algorithms, like RSA and ECC, that currently secure the internet, creating a "quantum apocalypse" scenario for digital communications if not addressed proactively. In the shorter term, the discovery of a major vulnerability or a practical flaw in a widely used standard like AES could have a catastrophic impact on digital security and trust. Another persistent threat is the human element, specifically the "insider threat." A malicious or simply negligent employee with legitimate access to cryptographic keys can easily bypass encryption controls and exfiltrate sensitive data. Finally, a contentious political and social threat comes from governments demanding the creation of "encryption backdoors" or "exceptional access" mechanisms for law enforcement purposes. Security experts argue that any such backdoor would inevitably be exploited by malicious actors, fundamentally weakening the security and trustworthiness of encryption for everyone.
Explore More Like This in Our Regional Reports:
- Business
- Art
- Causes
- Crafts
- Dance
- Drinks
- Film
- Fitness
- Food
- Oyunlar
- Gardening
- Health
- Home
- Literature
- Music
- Networking
- Other
- Party
- Religion
- Shopping
- Sports
- Theater
- Wellness
- Technology
- Cryptocurrency
- Psychology
- Internet
- Ecommerce
- Family
- Others


